Remote Session
Last updated on 22 October, 2024Overview
The Remote Session feature in LogicMonitor provides a secure way to remotely access and operate on devices from within your LogicMonitor portal. Remote sessions are enabled via the use of Apache Guacamole, a clientless remote desktop gateway that requires no plugins or client software.
The remote session protocols available for establishing a communication stream between your account and the Collector monitoring your device are RDP, SSH, and HTTP/S. The protocol must be configured for the device endpoint in order to be able to establish a remote session connection. Remote sessions take place through a secure SSL connection supported by the protocol (HTTP/S you have the option to use SSL or HTTPS or just HTTP).
Note: The maximum duration for a remote session is 60 minutes. After 60 minutes, whether you are currently interacting with the remote device or not, the session will time out.
Initiating a Remote Session
To initiate a remote session:
- From the Resources tree, select the device you wish to access and, from its detail view, click the “Manage” arrow and select “Remote Session” and the desired protocol from the subsequent dropdown menus.
Any protocol can be used if properly configured on the device, but typically RDP is used for Windows devices and SSH is for non-Windows/Linux devices.
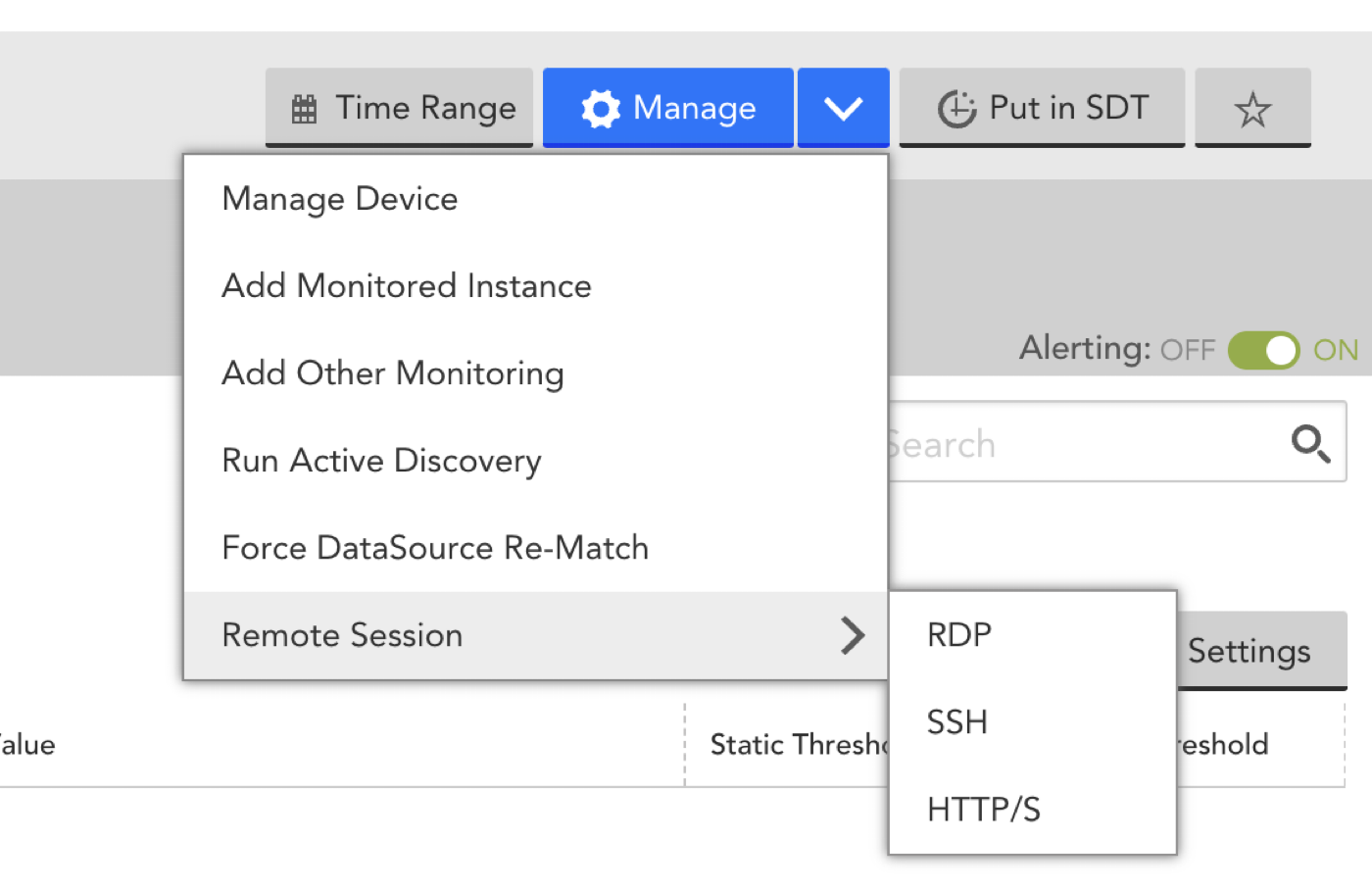
Note: Collector version 28.600 or a higher numbered version is required to use HTTP/S. If a lower numbered Collector version is in use, these protocol selections will be disabled and a message to that effect will be displayed upon mouse-over. - A new browser window opens, prompting you to enter the account and password for your device.
Note: You must log into the device within three minutes of initiating the remote session or the session will time out.
Note: LogicMonitor does NOT currently support SSH key authentication or Network Level Authentication on Windows.
- Once the remote session is initiated, select Control+Alt+Shift to open the Apache Guacamole clipboard for copy-and-paste functionality or directly input new command lines.
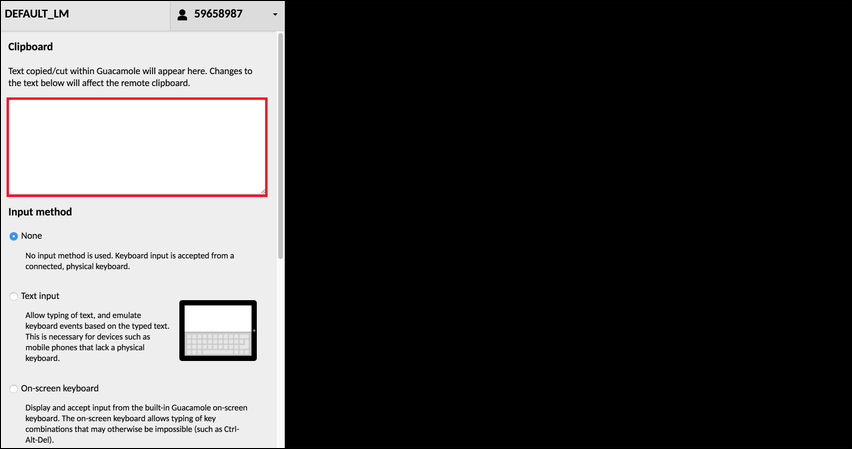
Note: Some platforms are not supported by the Apache Guacamole clipboard copy-and-paste feature, as discussed in the Apache Guacamole Frequently Asked Questions.
Remote Session Device Properties
LogicMonitor supports several Remote Session protocol properties that you can use to override default connection behavior.
| Remote Session Protocol | Property Name | Default Value | Req’d? | Description |
| SSH | remotesession.ssh.port | 22 | no | Populate to override default SSH port value. |
| RDP | remotesession.rdp.port | 3389 | no | Populate to override default RDP port value. |
| HTTP/S | remotesession.http.ssl.enable | true | no | SSL is enabled by default. Enter false if you are using HTTP instead of HTTPS. |
| remotesession.http.port | 443 (for HTTPS by default); 80 (for HTTP if ssl.enable is false) | no | Populate to override the default port for the HTTP/S connection. Defaults are 443 for HTTPS and 80 for HTTP. | |
| remotesession.http.rootpath | / | no | Specify the HTTP/S path. By default the root path is used. | |
| remotesession.http.proxy.version | v1 | no | Supported values: v1 and v2. Enables you to switch between proxy versions. If you specify invalid version (for example, v5) then by default v1 is selected.
Note: When you set the property, remove old cookies from the browser for remote-session URLs and then create the remote session. | |
| RDP and SSH (deprecated) | remotesession.port=[portnumber] | Values set for SSH or RDP ports using one of the properties listed above will override the value set for this property | no | This property is deprecated, but still supported. It carries the port number required to RDP/SSH into the device (typically only used if a non-standard port is required). If you are setting up Remote Session for the first time, use the above SSH and RDP port properties. |
| remotesession.protocol=[RDP or SSH] | n/a | no | Previously used to indicate the protocol (RDP or SSH) for the device (rather than allowing LogicMonitor to automatically determine protocol based on device type), but with the addition of new protocols and the ability to manually select preferred protocol upon remote session initiation, this property is fully deprecated and no longer used. |
For more information on adding/updating properties for a resource, see Resource and Instance Properties.
Access Controls
Remote sessions do not change the underlying authentication and access control of the device operating system, but they do allow access to the device in situations where it may not otherwise be possible. For this reason, LogicMonitor has several controls in place that serve to limit access to the Remote Session feature on a global or more granular basis:
- Account-wide control. Remote Session can be disabled on an account-wide basis from LogicMonitor’s account settings. For more information, see About the Account Information Page.
- Per-Collector control. Remote Session can be disabled on a per-Collector basis, effectively disabling the feature for all devices assigned to that Collector. This is accomplished by manually updating the remotesession.disable setting found in the Collector’s configuration file to “true”. For more information on editing a Collector’s configurations, see Editing the Collector Config Files.
- Role-based access control. Remote Session is defined as a separate user privilege. As discussed in Roles, a role can be given the ability to initiate remote sessions on all devices, those in a specific group, or no devices at all.
Requirements and Limitations
Please note the following requirements/limitations:
- The protocol used to initiate a session must be enabled on the device to which you are attempting to connect.
- The remote session connection will not work if “RDP Security Layer” is enabled for Window Server 2008’s Remote Desktop.
- If working with non-Windows or Linux devices (e.g. Cisco controllers), you will most likely use SSH to establish communication. However, you may need to manually do one of the following to ensure a proper connection:
- Ensure default SSH configurations are in place
- Enable username/password access for SSH on the device
- Make sure that the IPs used by the relay server are allowed (added to allow list). See LogicMonitor Public IP Addresses and DNS Names for a complete list.
- HTTP/S protocol limitations:
- Domain/device redirects. Redirects to another domain/device (e.g.
https://targetdevice.com/login.jsp redirects to
https://anotherdevice.com/login.jsp) are not supported. - Port redirects. Redirects to another port (e.g. http://targetdevice.com/index.jsp redirects to https://targetdevice.com/index.jsp, where the port changes from 80 to 443). For port redirects, use the properties listed in the Remote Session Device Properties section of this support article to specify the HTTP/S port, use of SSL, and path.
- SSO login redirects. This affects vCenter remote session logins. In addition, if the page is requesting resources out of target device domain and is not accessible from a public browser (e.g. the webpage is requesting another device’s CSS resources which are not accessible from the browser directly), those resources will not be available via the remote session.
- Link parsing in the HTTP body request. During a remote session, the HTTP/S protocol uses a RelayServer which works as a reverse proxy to return a page when the HTTP/S connection is initiated. It only acts upon HTTP requests and responses in the header in order to determine that the link is valid and for the same host. This affects some devices, such as Cisco UC devices.
- If the HTTP RemoteSession fails then add remotesession.http.proxy.version property and set its value as v2.
Note: When you set the property, remove old cookies from the browser for remote-session URLs and then create the remote session.
- Domain/device redirects. Redirects to another domain/device (e.g.
Note: While not possible with some redirects, if they are known the path can be added as the value for the remotesession.http.rootpath property to connect to the redirect page directly.
