Delinea Vault Integration
Last updated - 05 March, 2025
Note: Thycotic has been rebranded as ‘Delinea’. Although we have replaced Thycotic with Delinea in Support documentation, you will still find ‘Thycotic’ in some configuration properties.
LogicMonitor stores sensitive information including credentials, secrets, and so on for hosts, devices, and services. LogicMonitor also supports integration with Credential Vault and provides users control over credentials using their own credential vault. LogicMonitor Collector supports integration with Delinea as a Credential Vault solution. For more information, see Delinea Secret Server from Thycotic.
LogicMonitor Delinea Secret Server integration uses the OAuth2 token-based REST API of the Delinea Secret Server. In this approach, the OAuth2 token is used for authentication, which performs the various entity operations of the Delinea Secret Server.
The Delinea Secret Server offers REST API to manage various entities and provides version-specific Secret Server (SS) REST API guides. You must refer the correct version of the Secret Server guide. For more information, see APIs and Scripting from Delinea.
Delinea Collector Agent Configuration Settings
You must configure the following Delinea vault configurations in the agent.conf settings. To access the agent.conf settings, follow these steps:
- In LogicMonitor, navigate to Settings > Collectors.
- Under the Collectors tab, select the collector with whom you want to integrate Delinea vault.
- Select the More option and then select Collector Configuration.
- Under the Agent Config tab, configure the following vault properties. You can add the Delinea vault configurations anywhere in the agent.conf settings.
| Configuration Name | Type | Default Value | Description |
vault.bypass | Boolean | True | If the value is true, the collector will not initiate the vault API request.If the value is set as false, the collector will initiate the vault API request. |
vault.thycotic.session.timeout | Integer | 20 minutes | It is the time (in minutes) that the OAuth2 access token is valid. The token expires after this duration. |
vault.thycotic.max.tokenrefresh.allowed | Integer | 3 | It is the maximum number of times you can refresh the OAuth2 access token. You can refresh the token to get the access token for the user using the refresh_token information (without using user credentials). |
vault.thyotic.secret.path.name.id.cache.expiration | Integer | 20 minutes | It is the time (in minutes) after which the cache expires. The cache stores the secret path, including the FolderName and SecretName, which is linked to the secret ID. The lmvault keys use this cache internally to retrieve the secret ID based on the secret path. |
- Select Save and Restart.
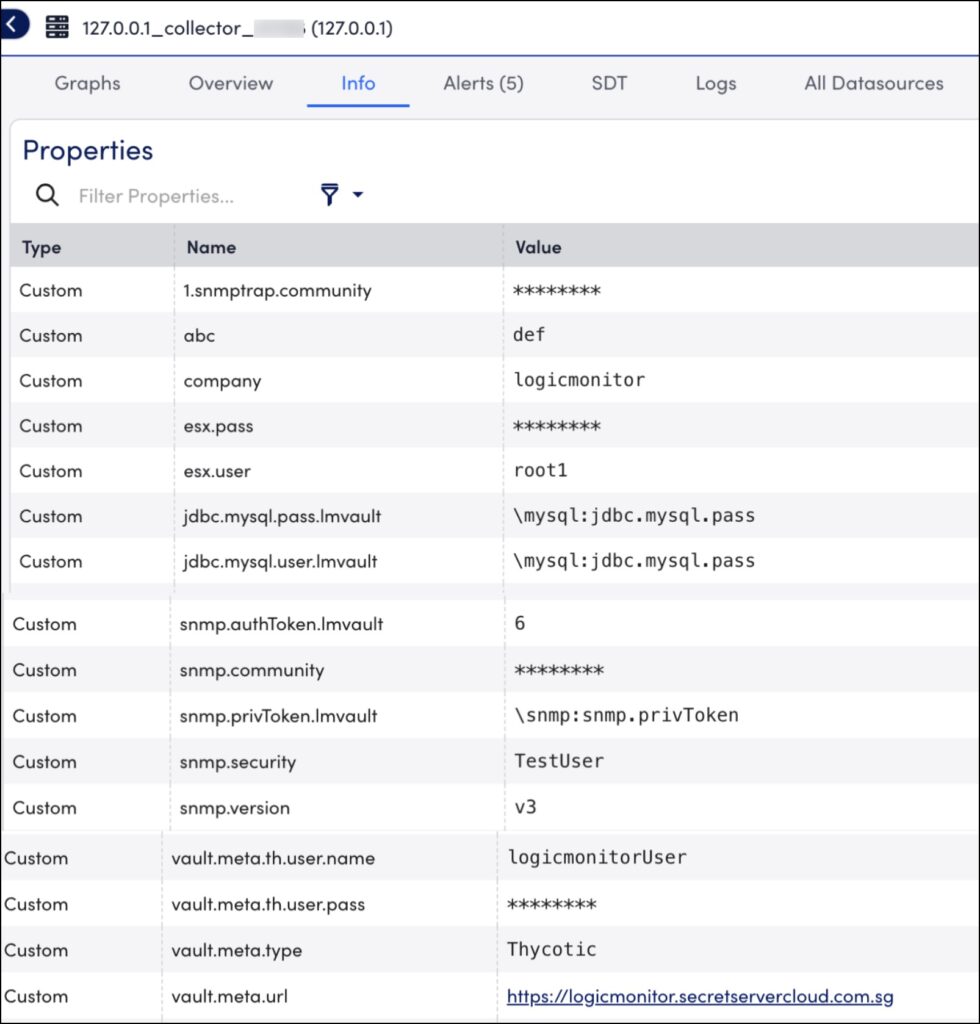
Delinea Vault Properties
Vault properties, such as vault metadata and vault keys for the collector, can be configured at the device or device group level.
The vault metadata properties are as follows:
| Vault Metadata | Description |
vault.meta.url | It is the URL of the vault. This URL must only contain the folder and application ID. |
vault.meta.type | It is the type of the vault. Use the value Thycotic to connect with the Delinea Secret Server. |
vault.meta.th.user.name | It is the username of the Delinea Secret Server account. The username and its password is used to get the bearer authentication token using the Secret Server OAuth2 API. |
vault.meta.th.user.pass | It is the password of the Delinea Secret Server account. The username and its password is used to get the bearer authentication token using the Secret Server OAuth2 API. |
vault.meta.header | The headers required for HTTP GET request. The value of this custom property is the header separated with “&“, the header key value is separated with “=”For example—vault.meta.header – Content-Type=application/json&Accept-Encoding=gzip, deflate, br |
Delinea lmvault.keys Configuration
You can configure lmvault.keys in the following three ways:
- Secret ID—lmvault key value can be configured with the secret ID. This is the most efficient method and is also recommended by Delinea.
- Secret path—LogicMonitor provides an out-of-the-box approach for configuring the lmvault.key value. lmvault value consists of the secret path and secret name.
LogicMonitor makes the Delinea API call to get the secret ID of the secret path. The secret ID is used to retrieve credentials.
Note: As this approach requires additional API calls, you must use this approach only when required.
- A combination of secret ID or secret path along with a Delinea field—You can configure devices to pull the secret values for a property from the secret ID or secret path. The field name is attached to the property to fetch the secret value from the Delinea field. The
.lmvaultproperty is configured to append the information of the Delinea field within the enclosed symbol “<>” at the end. You can use the templateRecordID<FieldName>/RecordPath:Name<FieldName>.
Example
| Vault Property | Customised Field |
|---|---|
ssh.user.lmvault | 9<username> |
ssh.pass.lmvault | 9<password> |
snmp.security.lmvault | 15<snmpsecurity> |
snmp.privToken.lmvault | 15<privtoken> |
ssh.pass.lmvault | \allsecrets\ssh:ssh.pass<password> |
If you choose to follow the secret path to configure lmvault.keys, LogicMonitor supports the following two approaches to retrieve the secret ID using the secret path:
- Default Approach—LogicMonitor searches for the folder and secrets. In this approach, the folders and the secrets are searched to form the secret_path_name relation with the secret ID.
- Delinea Reporting—LogicMonitor uses Delinea reporting to retrieve the secret ID using a secret path.
Note: Ensure that you can access the Delinea Report “What secrets a user can see” in the Delinea Secret Server portal. For more information on configuring the Delinea reports, see Configuring Delinea Report Properties section.
Requirements for Integrating with Delinea Vault
To integrate LogicMonitor Collector with Delinea Vault, you need the following:
- You must have EA Collector 30.102 or later installed on your machine. For more information on integrating Delinea Vault with LogicMonitor Collector, see Integrating Credential Vault Properties.
- Verify access of the Delinea Secret Server API using the Postman client.
- To configure Delinea report properties, you must configure Delinea vault.
Configuring Delinea Vault
To configure Delinea vault, follow these steps:
- Configure the vault properties on the devices. The properties consist of the vault metadata and vault keys. For more information, see the Delinea Vault Properties section.
- In the agent.conf settings, set the value of
vault.bypasstofalse. For more information, see the Delinea Collector Agent Configuration Settings section.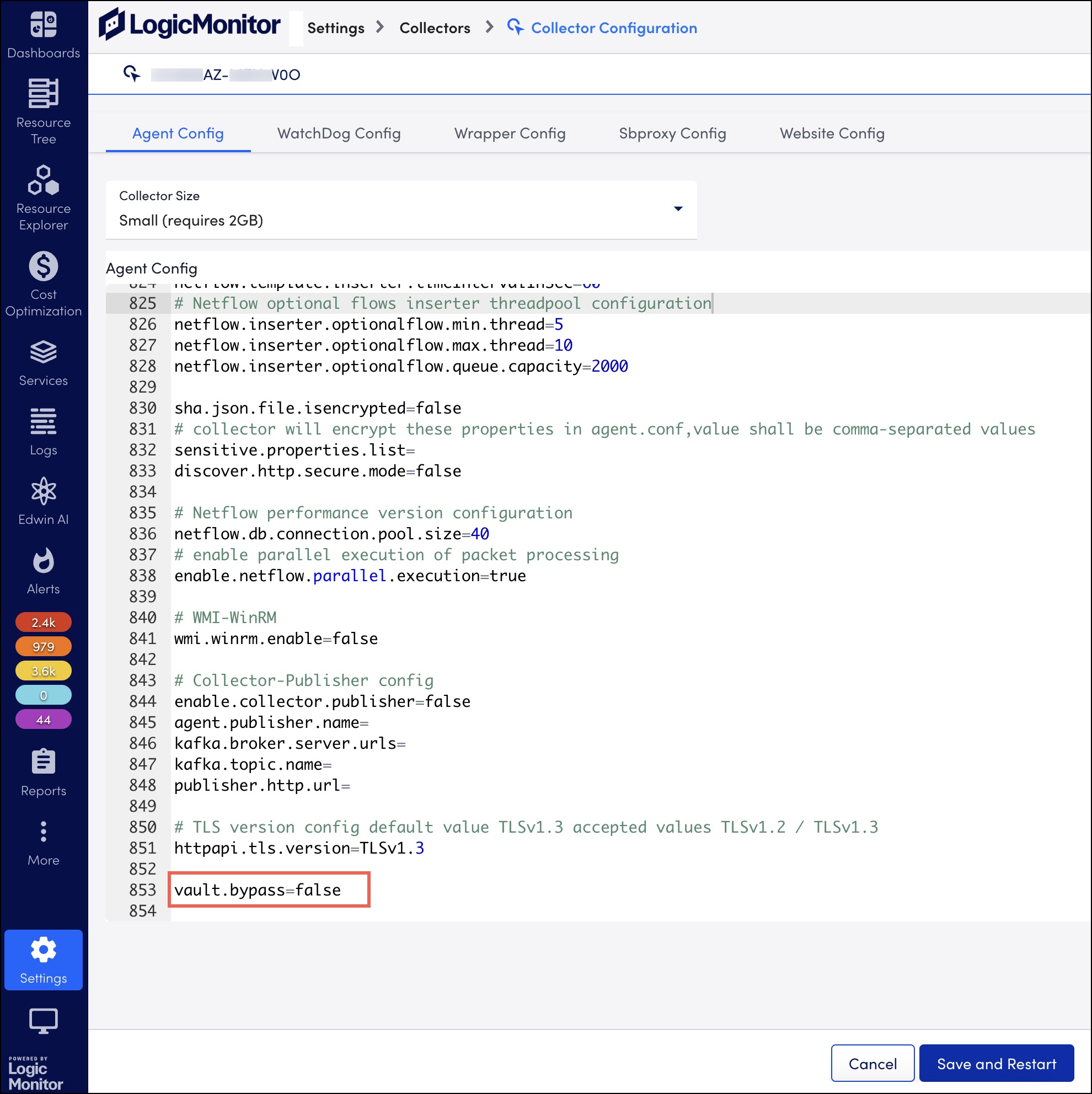
- Select Save and Restart.
Note: You can modify the default agent.conf settings as required. For more information, see Delinea Collector Agent Configuration Settings section.
Configuring Delinea Report Properties
To configure Delinea report properties, follow these steps:
- In LogicMonitor, navigate to Settings > Collectors.
- Under the Collectors tab, select the collector with whom you want to configure Delinea report properties.
- Select the More option and then select Collector Configuration.
- Under the Agent Config tab, configure the following Delinea report properties.
| Property Name | Type | Default | Description |
|---|---|---|---|
vault.thycotic.secret.report.access.enabled | Boolean | false | It indicates if the access to the Delinea Secret Server report is enabled or not. Before enabling this property, ensure that you have all the access to users, reports, and so on for the reporting. If you do not have the access, it may lead to API access denied issues. |
vault.thycotic.secret.report.id | Integer | Correct report ID value | It specifies the report ID of the “What Secrets a User Can See” report, which provides a system report for secrets. |
- Select Save and Restart.


