Credential Vault Integration for the LM Collector
Last updated on 15 October, 2024The Credential Vault integration for the LogicMonitor Collector makes it possible to store and manage sensitive information (including credentials and secrets for hosts, devices, services, etc.) in an external credential vault.
LogicMonitor Collector supports the following vault integrations:
Note: Support for the Credential Vault Integration was added in EA Collector 29.108. Refer to the relevant vault integration topics for supported Collector versions.
Integrating Credential Vault Properties
- In LogicMonitor, navigate to Resources > Device> required Collector > Info tab.
For more information on vault properties, see Adding Vault Properties. - Click Settings on the left panel and select Collectors.
- Select the required Collector and click the Settings icon under the Manage column.
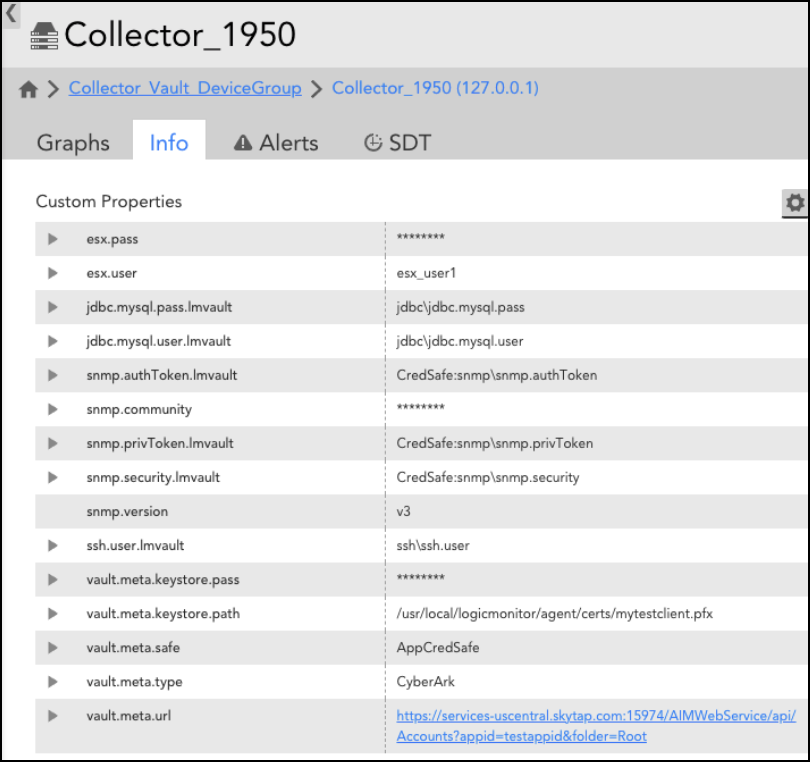
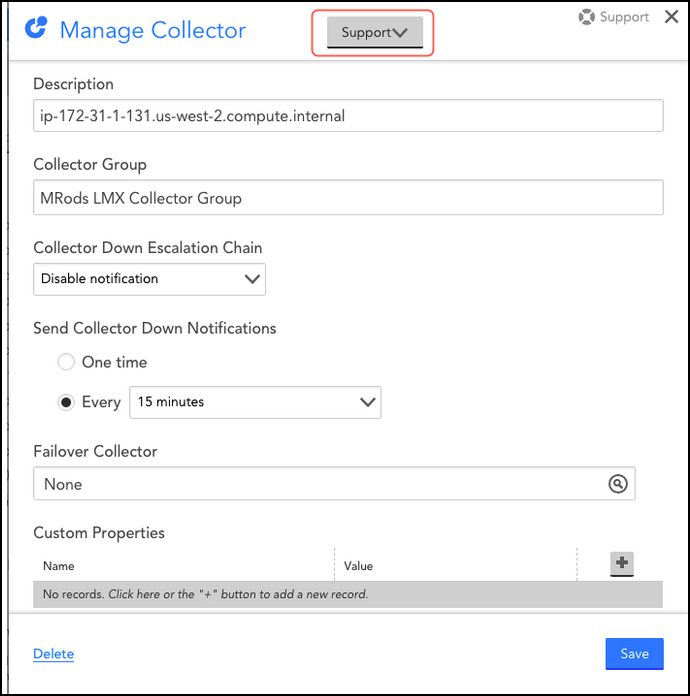
- On the Manage Collector dialog box, select Collector Configuration from the Support drop-down list.
- Ensure to set the vault.bypass value to false in agent.conf. Additionally, you can add the required agent configuration properties to set the Collector. For more information, see Collector Configurations.
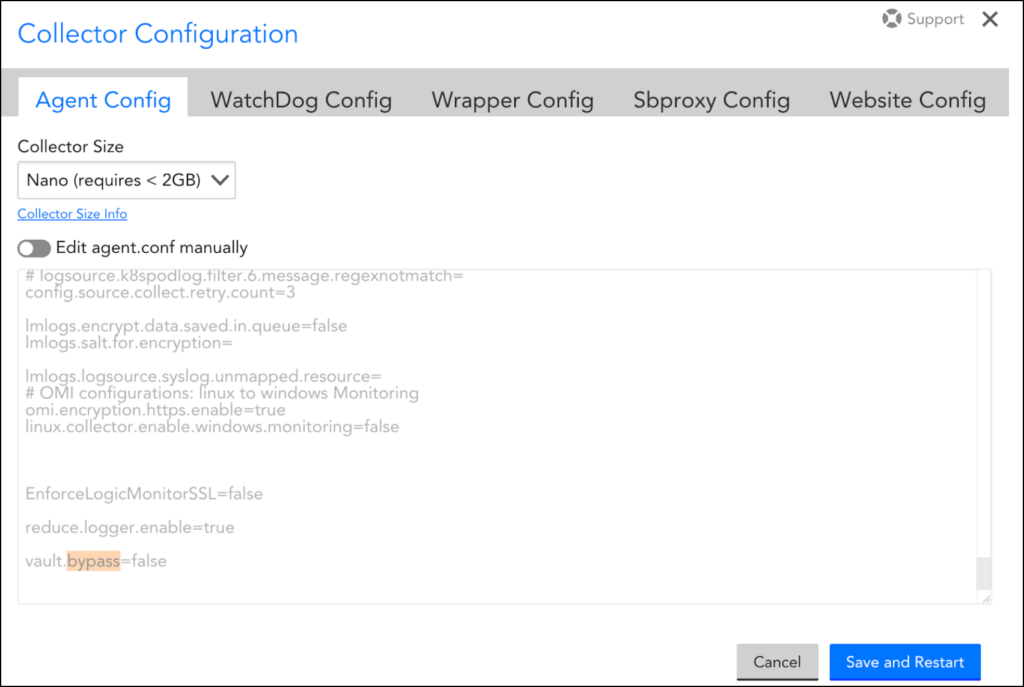
Collector Configurations
The following table lists the configuration properties to set in the Collector agent.conf.
| Property | Type | Default | Description |
| vault.bypass | Boolean | TRUE | If the value for the property is true, the vault API calls won’t happen. Note: You must set the property to false, to enable the vault API calls. |
| vault.credentials.cache.expirationtime | Integer | 60 | The property specifies the value in minutes for the expiry of the credential in the vault cache on the collector. After this time, the credentials in the vault cache will expire. |
| vault.credentials.refresh.delay | Integer | 15 | Controls the Credential Vault integration cache expiration refresh delay in seconds. |
| vault.url.cache.enabled | Boolean | FALSE | The property specifies whether the URL cache is enabled or not. By default the property is set as false; however, if the property is set to true the collector caches the URL and secret value. If the URL for lmvault property is found in the URL cache, the respective secret value is returned, else the API call is made to fetch the secret from the vault. Setting this property to ‘true’ should resolve API rate-limiting issues. |
| vault.url.cache.max.size | Integer | 1000 | The property defines the number of URLs that will be stored in the cache. |
Adding Vault Properties
For adding vault properties, such as Vault Metadata and Vault Keys, navigate to Resources > Device > Collector, click Info on the Collector page.
Vault Metadata
The following table lists the Vault Metadata properties.
| Property | Description |
| vault.meta.url | The URL of the vault. |
| vault.meta.type | The type of vault. |
| vault.meta.header | The headers are required for HTTP Get Request. The value for this custom property would be the header separated with & and the header key value separated with = as shown in the below example: vault.meta.header – Content-Type=application/json&Accept-Encoding=gzip, deflate, br |
Vault Keys
Vault keys need to be specified at the device level with suffix .lmvault.
| Property | Description |
| .lmvault | The custom property for which value should be retrieved from the Vault must be specified at the device level by adding suffix .lmvault. The value of such property would be the path of the key in the Vault. For example: ssh.user.lmvault = ssh\ssh.user |
