Event-Driven Ansible Integration Setup
Last updated on 04 September, 2024You can integrate LogicMonitor with Event-Driven Ansible to take remediation steps for an alert. For example, when a web server is down, the Ansible event can restart the web server when it receives alert from LogicMonitor.
Setup of LogicMonitor’s alert integration for Event-Driven Ansible involves the following steps:
- Configuring Event-Driven Ansible from LogicMonitor Portal
- Generating an Ansible Token
- Installing and Configuring LogicMonitor Plugin for Event-Driven Ansible
Configuring Event-Driven Ansible from LogicMonitor Portal
- In LogicMonitor, navigate to Settings > Integrations.
- Select Add Integration.
- From the Add Integration pane, under Automation Integration, select Ansible.
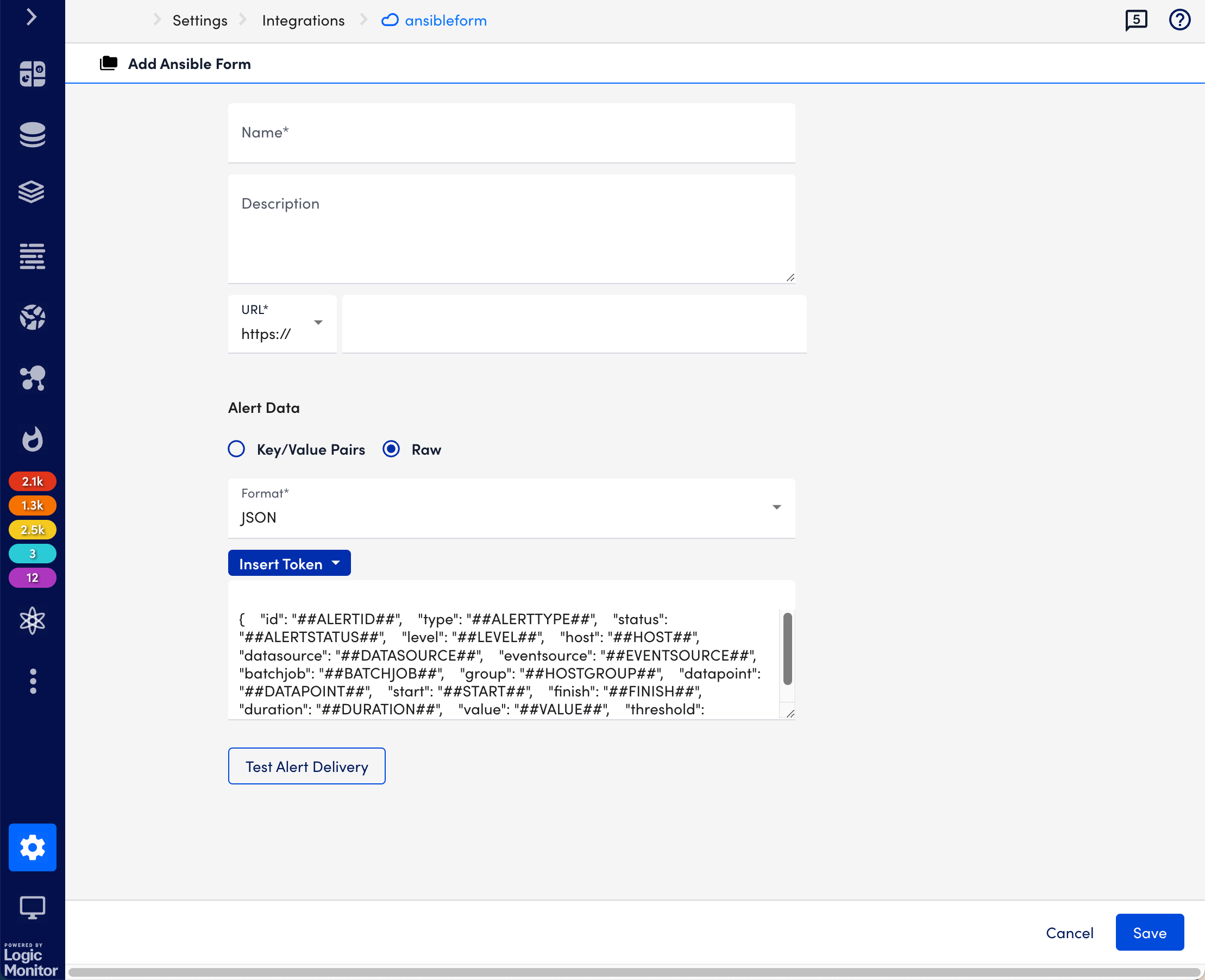
- Enter a name and description for the event-driven Ansible integration.
- Enter the URL at which the webhook event source is hosted.
- From Alert Data, select key and value pairs or tokens to customize the alert message.
- Select Key/Value Pairs, select Add Record, provide key Name and Value, and then select Apply.
- Select Raw, select Insert Tokens, and theninclude the tokens you want for the alert message. The following tokens are available:
- ##ADMIN##
- ##ADMIN.PHONE##
- ##ADMIN.EMAIL##
- ##ADMIN.PAGER##
- ##ALERTTYPE##
- ##ALERTSTATUS##
- ##MESSAGE##
- ##ALERTID##
- ##EXTERNALTICKETID##
For more information, see Tokens Available in LogicModule Alert Messages.
Note:- The Alert message is sent only in JSON format.
- By default, as an example, some tokens are included in the Alert Data message section. You can edit this section by adding tokens using the Insert Token button.
- Select Save.
Generating an Ansible Token
To generate an Ansible token, you must reopen the integration you have configured. For more information, see Configuring Event-Driven Ansible from LogicMonitor Portal.
- Navigate to Settings > Integration, and then select Manage associated with the Ansible integration you have configured.
- Select Generate Ansible Token to generate Ansible token.
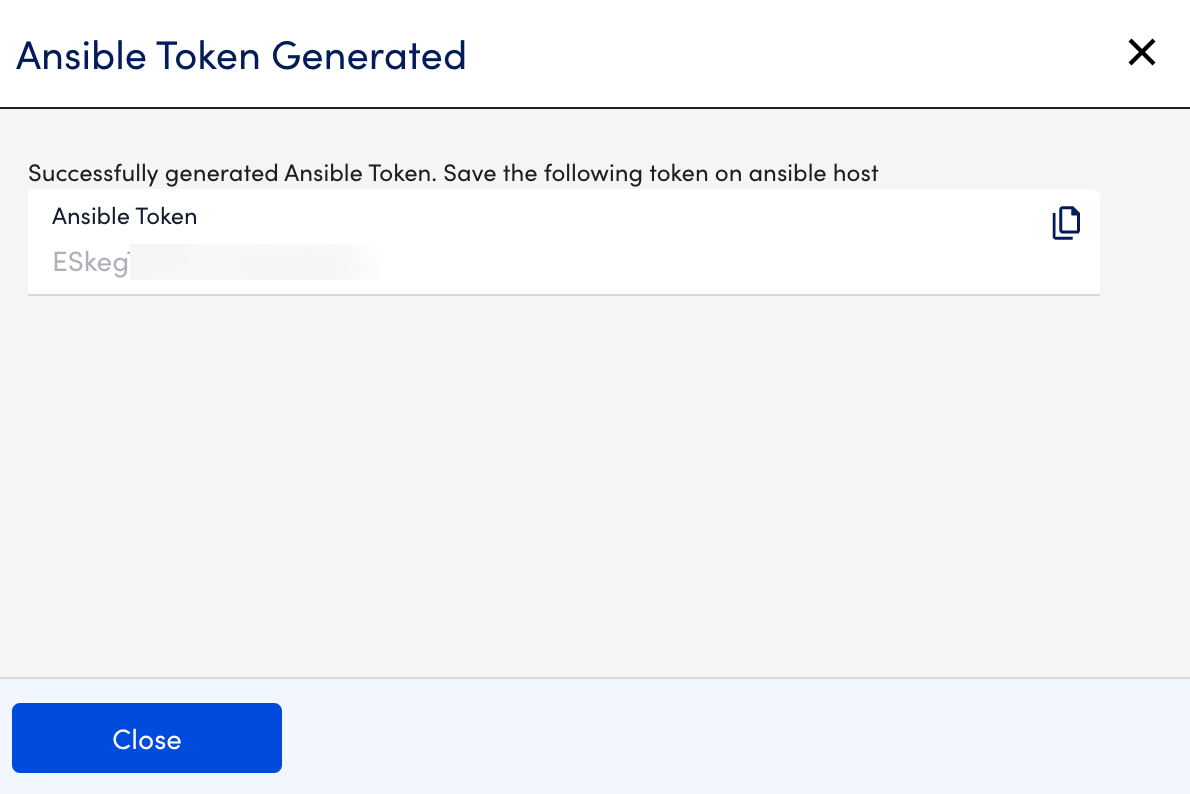
- Copy the generated token. The token needs to be copied and stored on the Ansible host so that it can be verified.
Recommendation: Ensure you securely store and transfer the Ansible token from your LogicMonitor portal to your Event-Driven Ansible plugin instance. You cannot access the generated Ansible Token after closing the message.
Installing and Configuring LogicMonitor Plugin with Event-Driven Ansible
To install and configure LogicMonitor plugin with Event-Driven Ansible, you:
- Must generate an Ansible token after configuring Event-Driven Ansible from LogicMonitor portal. For more information, see Generating Ansible Token.
- Must install Ansible Rulebook on your system. For more information, see Installing Ansible Rulebook.
Use the following commands to install and configure the LogicMonitor plugin with Event-Driven Ansible.
1.Install Logicmonitor Ansible plugin.
ansible-galaxy collection install logicmonitor.integration |
2. Create a file secure_vars.yml. You need to add the Ansible token you have generated after configuring Event-Driven Ansible from LogicMonitor Portal. For more information, see Generating an Ansible Token.
---ansible_token: [copied token] |
3. Encrypt the file using Ansible vault.
ansible-vault encrypt secure_vars.ymlNew Vault password:Confirm New Vault password: |
Note: You should remember the password used for encryption.
4. Create a rulebook or use one of the provided rulebook.
---- name: webhook alert Events hosts: localhost sources: - logicmonitor.integration.webhook: hosts: 127.0.0.1 port: 5000 vault_pass: '{{vault_pass}}' vault_path: '{{vault_path}}' rules: - name: start collector condition: event.payload.type == "agentDownAlert" action: run_playbook: name: logicmonitor.integration.start_lm-collector |
5. Pass in the required arguments.
Arguments can be passed directly in rulebook or as a variable from file or environment. For more information, see Usage in the Ansible documentation.
6. Run the plugin with the following command:
- Ansible rulebook sample command with variables from environment variable using option [“–env-vars vault_pass”]:
ansible-rulebook --rulebook rulebooks/AgentDownMitigation.yml -i rulebooks/inventory.yml --verbose --env-vars vault_pass - Ansible rulebook sample command without passing environment variable :
ansible-rulebook --rulebook rulebooks/AgentDownMitigation.yml -i rulebooks/inventory.yml
Once you have configured the plugin, you will receive the alerts for the Ansible events source.
