Logs Search Cheatsheet
Last updated - 23 July, 2025
The following provides tips for how to work with the query language in LM Logs. For more information, see LM Logs query language.
Reserved Fields
LogicMonitor reserved fields are indicated by a leading underscore. If you’re not sure what to search for, you can always start by typing a underscore into the query bar to see the list of reserved fields.
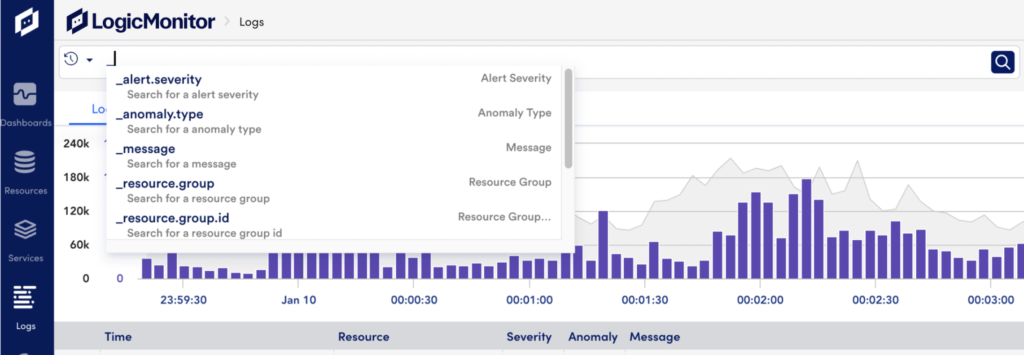
| Field | Description |
| _alert.severity | The severity level of alerts, which can be warning, error, critical. |
| _anomaly.type | The type of anomaly detected, such as never_before_seen. |
| _message | The message field of the log. If a field name is not specified, the _message field is the default search field. |
| _resource.group | The full path of the resource group. |
| _resource.group.id | The resource group ID. These values may not be provided by autocomplete. |
| _resource.group.name | The name of the resource group, which is the part of the full path after the last front slash. |
| _resource.id | The ID of the monitored resource. These values may not be provided by autocomplete. |
| _resource.name | The name of the monitored resource. |
| _tenant.id.{} | The tenant ID of the monitored resource. |
| _user.agent | The user agent name included in the log header. |
| _resource.attributes | The resource mapping information that is used to correlate the logs with monitored resource. |
| _coalesced.fields | Excess metadata entries that are added as a separate key in a string format. The excess metadata entries are added to this field based on the following criteria: The length of the key exceeds the maximum limit. The key has an invalid regex format. |
| _lm.collectorId | The ID of LM Collector that processed the log. |
| _lm.logsource_id | The ID of LogSource applied to the log. |
| _lm.logsource_name | The name of LogSource applied to the log. |
| _lm.logsource_type | The type of LogSource applied to the log (syslog, wineventlog, and so on). |
Note: You should avoid using reserved field names when configuring the sending of log data for ingestion. Using reserved field names when naming custom log metadata fields may cause unexpected behavior when ingesting log data.
Logical Operators
Searching with logical operators supports NOT, AND, and OR to combine filters.
| Operator | Description | Example |
| AND | Search for logs that contain all of the fields and values specified. | _resource.name=winserver01 AND type=wineventsDisplays all logs associated with winserver01 and also contains winevents in the type field. |
| OR | Search for logs that contain one or more of the fields and values specified. | _resource.group.name="Linux Servers" OR _resource.name~linuxDisplays all logs for resources in the “Linux Servers” Resource Group or any resource that contains “linux” in the Resource Name. |
| NOT | Search for logs except any of the fields or values specified. | NOT _resource.name=winserver01Displays all logs from any resource except winserver01. |
Comparison Operators
Run queries comparing number values included in log message or metadata.
| Operator | Description | Example |
| For example <, >, and >= | Parse out specific number values in messages or metadata. | _size>=1500Displays all logs with volumes larger than or equal to 1500 bytes. |
Advanced Search Operators
Advanced searches include aggregation, processing, and formating operators that can help you to refine and modify your search results. For more information, see Advanced Search Operators.
Pattern Matching
Keyword Match
Any free text search will search only the raw log message for matches.
| Query | Description | Example |
keyword | Searches and displays only logs where the keyword is found in the message field. Use when you want to search all log messages for a string or value. This works the same way as previous LogicMonitor Logs keyword search. | errorOnly logs that contain “error” in the message field will be displayed in the logs table. |
Exact Match
Returns events if the pattern exactly matches the field value.
| Query | Description | Example |
field=word | Searches and displays only logs where field has the value word. Use when you know the exact value you want to match. | _resource.name=winserver01Only logs associated with resource “winserver01” will be displayed in the logs table. |
field=word1,word2,word3 | Searches and displays only logs where field has the value word1 OR word2 OR word3. The commas represent an OR operator. Use when there are multiple exact values you want to match. | _resource.name=winserver01,winserver02,winserver03Only logs associated with resources “winserver01”, “winserver02”, or “winserver03” will be displayed in the logs table. |
field="word with special characters" | Uses double quotes to capture a special character in the field value. Finds all logs where field equals “word with special character”. Use when you know the exact value and the value includes a special character. Double quotes are required when there are special characters, such as a hyphen or a whitespace, in the pattern. The non-special characters set is [a-zA-Z0-9*]. | _resource.name="win-server01"Only logs associated with resource “win-server01” will be displayed in the logs table. |
Fuzzy Match
Returns events using glob expressions to match similar field values. Fuzzy matching is not case sensitive.
| Query | Description | Example |
field~word | Searches and displays only logs where field contains word. Use when you specifically want a fuzzy match instead of an exact match. | _resource.name~winserver01Only logs associated with resources that contain “winserver” will be displayed, this includes “winserver01”, “winserver02”, “winserver03”, “winserver03west”, and so on. |
field~word1,word2,word3 | Searches and displays only logs where field contains any of word1 OR word2 OR word3. The commas represent an OR operator. Can use when you want fuzzy match on multiple values. | _resource.name~winserver,linuxserver,firewallOnly logs associated with resources that contain “winserver”, “linuxserver”, “firewall”, etc. will be displayed. This includes resources such as “winserver01east”, “winserver03west”, “nonprodserver”, and so on. |
field~"word with special characters" | Uses double quotes to capture a special character in the field value. Finds all logs where the field contains “word with special character”. Double quotes are required when there are special characters, such as a hyphen or a whitespace, in the pattern. The non-special characters set is [a-zA-Z0-9*]. | _resource.name~"win-server01"Only logs associated with resources that contain “win-server01” will be displayed, this includes “win-server01”, “win-server01-east”, “win-server01-west”, and so on. |
Note: Regular expressions are used for queries with ~. Therefore the resulting output requires more computing resources and may take longer to complete.
Regex Match
Returns log events using regular expressions (Regex) to match field values. Regular expressions must be put inside of front slashes: /regular expression/.
Note: Note: The LM Logs query processing uses the Go RE2 regular expression library. For more information, see the Go RE2 documentation.
| Query | Description | Example |
/regex/ | Searches and displays logs where the message field contains the regular expression. Use when you want to find logs that contain certain structures (such as an IP address, unique identifier, and so on.) | /\b(?:[0-9]{1,3}\.){3}[0-9]{1,3}\b/Only logs that contain an IP address in the message field will be displayed. /\b[0-9a-f]{8}\b-[0-9a-f]{4}-[0-9a-f]{4}-[0-9a-f]{4}-\b[0-9a-f]{12}\b/Only logs that contain a unique identifier structure will be displayed. |
field~/regex1/,/regex2/ | Searches and displays logs where field contains any of regex1 OR regex2 expressions. Use when you want a regex match on multiple values. |
Troubleshooting
Parsing Errors
If there is a parsing error with your query, it may be caused by incorrect syntax.
- Check that all patterns that have special characters in the pattern are surrounded by double quotes.
- If there are double quotes, check that they are the correct double quote characters: “”
- Check that regular expression patterns include properly escaped characters within the “/ /”.
Timeout Errors
For raw logs, the timeout is 2 minutes. A timeout may occur when the time range for the search is too long, such as 30 days, and depends on the volume of ingested logs that you are searching. If the search has a timeout error, try decreasing the time range.

