Script EventSources
Last updated on 20 March, 2023Overview
You can use the Script EventSource collection method to detect and alert on any event. This may be useful if you have custom logging that can’t be monitored with the other EventSource collection methods (log files, windows event logs, SysLogs, and SNMP traps).
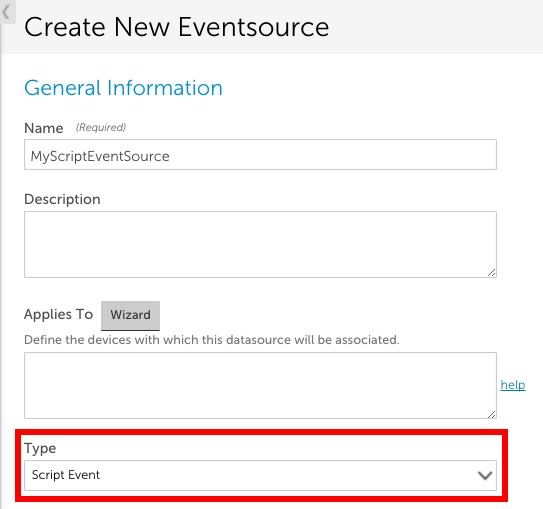
To create an EventSource using this collection method, set the EventSource Type field to ‘Script Event’ and either upload an external script or enter an embedded Groovy script.
Note: A maximum of 50 events can be discovered per script execution and a maximum of 100 events can be discovered per collector per minute.
Script Output Format
Regardless of whether it is an embedded or external script, the output needs to be a JSON object with an array of one or more events, like this:
The following fields can be used to describe an event in the script output:
NOTES:
- If your data structure is not JSON, you can use groovy JSON tools (e.g. JSONBuilder) to convert it. If you do use these tools, make sure to include this import statement in your script: import groovy.json.*
- Severity levels (warn | error | critical) are not case sensitive.
- You can add multiple custom attributes per event. These will simply need to be separated by a comma and newline. In the script output example below, we included customAttributes buffer.size and thread.number:
{ "events": [ { "severity": "warn", "happenedOn": "Thu Jun 01 09:50:41 2017", "buffer.size": "500m", "thread.number": 20, "message": "this is the first message", "Source": "no ival" }, { "severity": "warn", "effectiveInterval": 0, "happenedOn": "Thu Jun 01 09:50:41 2017", "buffer.size": "500m", "thread.number": 20, "message": "this is the second message" } ] }
happenedOn
LogicMonitor supports the following logfile date/times formats:
Example
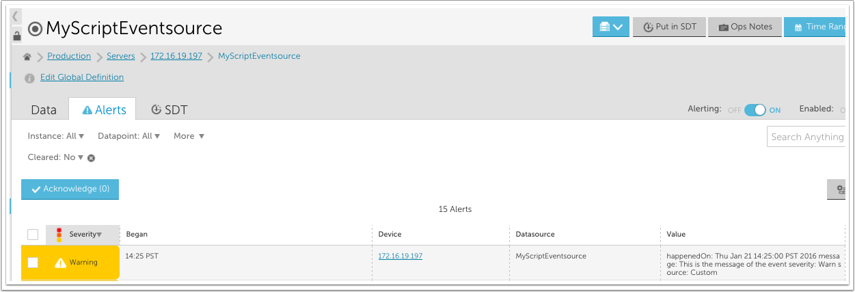
If the script output is:
The following alert will be triggered for the associated device: